Let's Talk About Irelands Cyber Security Strategy
Over Christmas, Ireland released it's National Cyber Security Strategy for implementation between 2019-2024. Considering that this was released, I believe on the 27th of December 2019, we're already a year behind which is a fantastic start... But let's dig into the detail of it and see where we stand going forward on the issue.
And I can't stress this enough. I do not want this to be seen as a hit piece against anyone at the NCSC, NSAC, An Garda Síochána, the Irish Defence Forces or anyone else in the national security apparatus of Ireland. I have met several of them over the past few years and while they are passionate and deeply care about the mission of protecting Ireland from cyber threats it is not their fault that they collectively work hard on information security issues and are plagued by issues like being under paid compared to others in the private sector and international colleagues and under resourced and having to deal with successive governments who have had no vision or care for information security and it's importance in the modern era.
This is a long post, so if you want the gist of my thoughts and you want to skip the detail, the final section has a summation of my thoughts and some form of a conclusion.
2: Vision
The vision of the document is pretty standard. It is based around Protect, Develop and Engage which you will see in other cyber security strategy documents. The protection aspect is based around protecting the State, the people of Ireland and the critical infrastructure of the State. It's pretty standard aspirational language to say this is where we would love to be in 2024 in an aspirational document. Not much more to add.
Personally I would love to see how we plan to find a balance of risks and costs because historically, the Irish Government has chosen to choose the cheap option that does not account for risks.
I would also love to know more details about developing the capacity of the state in the 5th Domain because everyone that I have talked to about this, be they cyber security students, lecturers, industry professionals or friends elsewhere think working for for the government on information security matters is insanity when I could be working elsewhere doing my best work and getting better paid for my work too. How do you plan to develop the capacity when only those who see the mission of protecting the state as more important than pay when people who would look at the world that way are few and far between?
Finally to engage others nationally and internationally on a free and open cyberspace. This is a goal I'm 100% behind because alone, we will not be able to solve all the issues we face. Working internationally will also allow us to develop key skills and finally, another goal is to integrate cyber into our diplomacy where we have secure missions to other nations that have the capacity to help other nations develop some of the capabilities that we have.
3: Objectives
-
To continue to improve the ability of the State to respond to and manage cyber
security incidents, including those with a national security component -
To identify and protect critical national infrastructure by increasing its resilience to cyber attack and by ensuring that operators of essential services have appropriate incident response plans in place to reduce and manage any disruption to services
-
To improve the resilience and security of public sector IT systems to better protect data and the services that our people rely upon
-
To invest in educational initiatives to prepare the workforce for advanced IT and cybersecurity careers
-
To raise awareness of the responsibilities of businesses around securing their
networks, devices and information and to drive research and development in cyber
security in Ireland, including by facilitating investment in new technology -
To continue to engage with international partners and international organisations to ensure that cyber space remains open, secure, unitary, free and able to facilitate economic and social development
-
To increase the general level of skills and awareness among private individuals
around basic cyber hygiene practices and to support them in this by means of
information and training
As goals in an aspirational document, these are fine. Personally, the key to this is the educational component. The pipeline of students doing cyber security is incredibly narrow, in part because of a small number of lecturers to teach the courses and in part because until very recently, ITB, now TU Dublin was the only place to get a solid education cyber. You could have a single module on it from various different colleges and universities, but you skimmed a huge area in a semester or went places like Trinity and Letterkenny which have societies to fill the gap that they both see in their education. And when Zero Days CTF comes around every year, the vast vast, vast majority of people taking part in the competition are current and former students from TU Dublin @ Blanchardstown, Trinity College Dublin and Letterkenny IT which is no coincidence.
Staying on education, educating all sectors of the economy of issues that they face will also be key. I don't know how best to accomplish this, but we have an economy where the vast number of people employed are employed in small and medium enterprise and these companies in the modern era are built on data. If anything were to happen to the database that stored this business critical information like a ransomware attack, it could shut down companies and that's no hyperbole. It's already happened. And not just that, if you follow ransomware, it's happening, all day, every day, everywhere and we're potentially one catastrophic zeroday away from having sectors or industries come to a halt. And there are very few companies that can handle something like, I believe historically it's been Saudi Aramco, Merck, Maersk Line and the NHS that have weather such a storm and done so not only because they had the know how to deal with such an issue and were somewhat prepared, but also because they had the cash reserves on hand required to deal with such attacks.
Education will also be key to dealing with the issues the general public faces from general cyber crime threats as in my personal experience, across nearly all age ranges there is very little conception of the threats they face, and arguably worse, what to do about such threats. And as someone who has tried to educate those who are not familiar with cyber security, the biggest problem I have personally found and I think it will be a major headache is going to be giving actionable information to people so that they can proactively raise their defence posture. It's all well and good telling a 60 year old to use a password manager, but it's one thing to tell someone to use it and to explain why they need to use it and how they should use it as simply as possible.
And this actionable information, what ever it is, is going to create narrow, technical, sniping arguments in the community because this is how we have operated as a discipline for the longest time which means that even if it works for the threat model, people may ignore the advice as noise rather than signal. But as professionals, we also need to be aware of the threat model that others are using and not apply it to ourselves and we need to stay abreast of the latest information and how that applies to threat models as advice like not writing down passwords is garbage advice in the modern era.
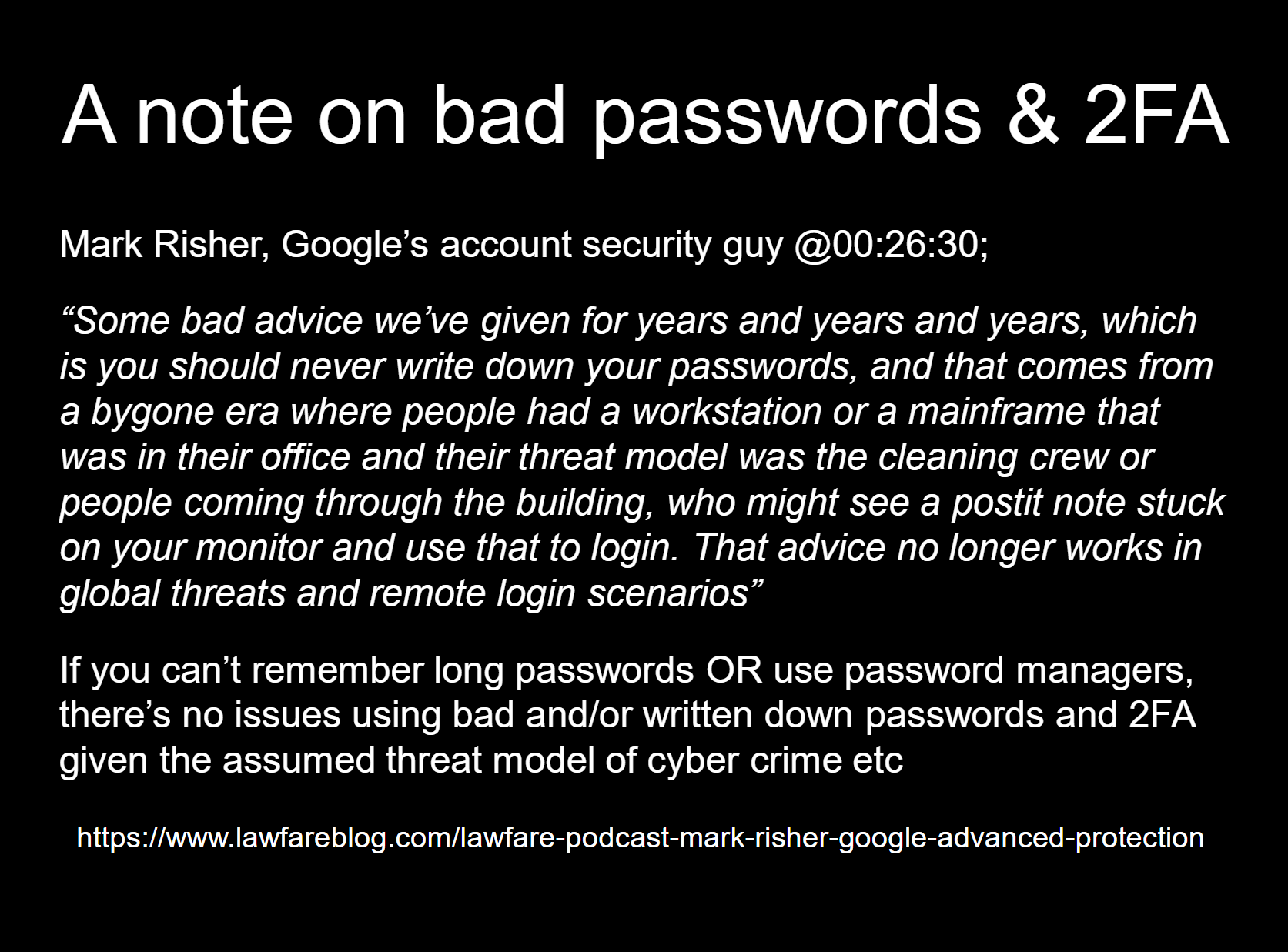
Finally on education, we also need to start adequately funding third level. It's good that we are putting computer science into second level, but there is a shortfall in spending on third level that some say is approaching crisis levels and since our economy is built on knowledge, this in general is not something that we can allow to happen.
With a start on the education, and a wider pipeline of people coming into the industry, then we can start to look at other goals we have in mind. The major issue is that there will be a lag time that we cannot afford between now and education coming online. The only solution to this is to attract the talent needed from the private sector and the bottom line, like it or not, is that there is a huge pay gap between what the private sector can afford and what the government will pay you. When I graduate at the end of this semester, my starting wage as a graduate in cyber security roles exceeds what a public sector wage would be by a significant margin. While it is a pay cut I would be willing to make in the national interest, I am in a very small minority.
4.1: Strategic Risks
While I have been quite critical up to now, this is where for a brief moment things look up. There is actually an element of strategy here. The government is aware that Great Power Politics is back in vogue again and that this creates certain threats and risks at a global geopolitical level and it has an impact on international relations and international security. Specifically the threats to Ireland are on trade and the impact of influence over technology vendors which for Ireland, which has a small, open vulnerable with a lot of multinational technology vendors, we are vulnerable to a change in trade or technology winds.
All of these technology vendors in Ireland host a large proportion of European Citizens data and the infrastructure required to host all of this data. This data we host means that we will have to secure some of the most important critical infrastructure in Europe and be aware that are critical to the functioning of our economy.
Ireland is also aware and makes it extremely clear that;
Recent years have seen the development and regular use of very advanced tools for cyber enabled attacks and espionage, and, likely for the first time, the physical destruction of Critical National Infrastructure by cyber enabled means. As such, the field of cyber security is characterised by an ongoing and high stakes technological arms race, ...
We are aware that other nations are flexing their cyber muscles with cyber tools like the Great Cannon, Stuxnet, Flame, BlackEnergy and Triton and that this is part of an ongoing arms race between the actors that are leading the charge of great power politics and also that these tools generally go after critical infrastructure. Though curiously, while we call it an arms race, and we mention no tools, we do not call them arms or weapons when reasonably under some definitions, you could.
What is unfortunate is that while we are aware of the great power politics and the ongoing arms race;
... that any single State can only exercise a degree of control over the operation of the network in its territory
While this is indeed true, this misses a critical point in that while in an open, liberal nation like Ireland, it is difficult to dictate how private industry should do procurement of their infrastructure, but this does not mean that the role the government can play in advising the the private sector in what infrastructure they buy or even use the sovereign powers of a government to prevent the purchase of infrastructure or level the market playfield if it is uneven or if it does endanger national security;
“We're committed to Huawei, they have been a good supplier”
— Defence Ireland (@DefenceIreland) January 31, 2020
Yes, because the Chinese government are subsidizing your cheap business model via them and the trade off is you let their shitty product spy on your customers. https://t.co/DD6QtuyAyw
So the Chinese government subsidize them, and they subsidize @eir who then put their shitty product in their network so they can compromise their customers. Customers like the Guards. pic.twitter.com/W1sMmQszEj
— Defence Ireland (@DefenceIreland) January 31, 2020
What’s worse is that the @eir CEO @carolan_lennon is going around citing that they have the Garda mobile contract when asked about Huawei security concerns by @adrianweckler as if its an endorsement. How long have they got the contract and was it before Huawei concerns arose?
— Defence Ireland (@DefenceIreland) January 31, 2020
It does not mean the government has a fig leaf for allowing the stupidity that is the body charged with protecting the national security of Ireland, from using subsidized, cheap Chinese network equipment on the Eir network. An issue so grave in the UK that Huawei's equipment placement in the network is extremely restricted and are effectively banned on networks in the United States, both for national security concerns related to what they know about Huawei. While you can argue about how much risk the UK is taking onboard vs the US approach, at least the UK had a discussion on the pros and cons on settled on an approach for good or ill. We didn't and we just let it happen and that has really mortgaged our future national security for a cheaper present installation of infrastructure, didn't discuss the risks and adopted it, no questions asked into the body charged with protecting our national security. That is a travesty that we cannot let continue if we are to take our national security seriously.
In some cliff notes, the government is aware of the issues that IoT devices could cause to security on a broad scale. That the government is not willing to pursue an intrusive system of monitoring, that there is a general issue around the openness of publicizing cyber attacks, even to the government and finally, the Government has set up the National Security Analysis Centre (NSAC) to assess technology in national security area'so that the government can receive good advice on the strategic threats we face as a nation.
4.2: Hybrid Threats
Hybrid Threats are;
... multidimensional, combining coercive and subversive measures, using both conventional and unconventional tools and tactics (diplomatic, military, economic, and technological) to destabilise the adversary.
In simpler terms, they are disinformation campaigns aimed at destabilizing and in general are difficult to counter by their nature. While they can use various techniques, the most common is the hack and dump method that Russia used extensively during the US Presidential Election of 2016. The EU is much closer to Russia than the US and countries like Estonia have been dealing with such hybrid war going back as far as 2007.
While I am by no means an expert on electoral security or hybrid warfare, I do see this as a massive threat. Ireland has, even throughout the Great Recession, had a mostly stable, open, liberal democracy and that could be a major factor in continuing to attract companies to come to Ireland in the wake of Brexit and if there is to be a more unified tax policy in Europe. It is good to know that at least we have a working group thinking about these issues and that we are contributing to European efforts to fight off disinformation and hybrid warfare and I hope that we are doing more than thinking and issuing a report with some thoughts in it and that if there are recommendations, they are followed as this is crucial to the future of our small nation.
Though someone on twitter who does know a great deal more about this is far from impressed;
The nod towards hybrid threats is frankly either pretty lazy or pretty incompetent. Nothing in here suggests the #Irish state is prepared to put in place the structures necessary to build intelligence on, analyse and counter false narratives and disinformation etc. pic.twitter.com/E07iVQDvxg
— Rory Byrne (@roryireland) December 27, 2019
4.3: Critical National Infrastructure and Public Sector Systems and Data
The Governments strategy until now has been that of risk reduction in the area's of
energy, transport, banking, financial market, health, drinking water supply and distribution and digital infrastructure
Which are defined in Annex II of EU's Directive on security of network and information systems (NIS Directive). And also online services, listed below, which are defined in Annex III of the same document
online marketplace, online search engine and cloud computing service
While the Irish Government's document does not make clear what they mean by reduction of risk, it isn't an information security term, the NIS Directive makes clear that it is the common risk mitigation strategy. It is also clear that while the NIS Directive covers certain sectors of importance, there is awareness that mitigating risks does not eliminate risk nor does it account for unknown unknowns. And that while the NIS directive does cover these sectors, it appears that an inventory of infrastructure has been done so that they are aware that the NIS directive does not cover all the infrastructure deemed critical and that some critical infrastructure is interdependent on other critical infrastructure such as the energy sector powering most of the other NIS sectors.
It's disappointing that the only real paragraph they have on securing public sector systems says that some departments and agencies are ISO 27001 compliant while others aren't and there's no mention of doing anything about the other departments and agencies. There are governance issues around classified information, be it Irish, shared with Ireland or stored in Ireland for whatever reason and that plans are underway to deal with this issue.
And finally;
The nature of these networks and technology is relevant also; being software defined and virtualised means that new types of security measures will likely be required in this sector to ensure the security of both the 5G network and of the services dependent on it.
At least the government appears aware that traditional threat models and defensive mechanisms will not work for 5G.
Appendix 1: Actions
This has been an extraordinarily long post by my standards so I'm not going to go point by point across all actions proposed, only the ones that I think are worth mentioning, but you can read them if you so desire in the document. Though I may not discuss the timeframes as I know that they have slipped already given the release date of the document.
Measure 1: The National Cyber Security Centre will be further developed, particularly with regard to expand its ability to monitor and respond to cyber security incidents and developing threats in the State.
Great idea and I really hope that it gets up and running sooner rather than later. Monitoring attacks in the state and gaining visibility into the threats that the state faces, as well as being able to fuse our data with that of international partners is key to protecting even the most basic of services provided by the government and is essential in staying abreast of emerging threats internationally. I worry though what 24/7/365 staffing of such an organization would look like and how it is intended to be staffed.
Measure 2: Threat intelligence and analysis prepared by the National Cyber Security Centre will be integrated into the work of the National Security Analysis Centre.
This is a common sense measure, but an important one and one that should have been done when both bodies were set up. If we have a bodying working analysing threats to national security, you need to feed them adequate intelligence so that they can accomplish their mission. This is also probably benefits from Measure 6 which will further develop threat intelligence efforts at the NCSC.
Measure 4: The NCSC, with the assistance of the Defence Forces and An Garda Síochána, will perform an updated detailed risk assessment of the current vulnerability of all Critical National Infrastructure and services to cyber attack.
This is basically a plan to deepen the vulnerability assessment of critical infrastructure which is well warranted as living in a post-Triton world as we have had the threat landscape expanded to include devices that were previously considered systems that would not be attacked.
Measure 5: The existing Critical National Infrastructure protection system will be expanded and deepened over the life of the Strategy to cover a broader range of Critical National Infrastructure, including aspects of the electoral system.
Measure 3 is not worth mentioning as it's basically just complying with an EU Directive but it feeds into this measure which is to say that while the NIS misses some aspects in infrastructure which we deem critical, we should assess the risks to all of our critical infrastructure.
Measure 7: Government will introduce a further set of compliance standards to support the cyber security of telecommunications infrastructure in the State.
Well, that vague... It's based on Directive 2018/1972 from the EU and the key thing that needs to be done at a high level is the following from paragraph (94);
Security measures should take into account, as a minimum, all the relevant aspects of the following elements: as regards security of networks and facilities: physical and environmental security, security of supply, access control to networks and integrity of networks; as regards handling of security incidents: handling procedures, security incident detection capability, security incident reporting and communication; as regards business continuity management: service continuity strategy and contingency plans, disaster recovery capabilities; as regards monitoring, auditing and testing: monitoring and logging policies, exercise contingency plans, network and service testing, security assessments and compliance monitoring; and compliance with international standards.
That may come from EU law but my god, there's more strategy in what the major issues are in that paragraph than nearly the entire document released by the Irish Government and that directive covers more of the wide spectrum of threats we face.
And a little late if you're worried about Huawei 5G equipment, it's a shame that the Irish Government is adopting regulations designed to deal with security of supply, access control to networks and integrity of networks and security incident detection capability, security incident reporting and communication AFTER such equipment has been adopted and when it is unknown if such equipment has a secure supply chain, can maintain network integrity or has adequate logging because the UK, even though they have allowed Huawei to operate at a restricted capacity in the 5G network, the UK NCSC are by no means impressed with Huawei gear.
Measure 8: The NCSC will develop a baseline security standard to be applied by all Government Departments and key agencies.
Is this a case of XKCD 927 or is this adopting ISO 27001 across the board? Measure 10 also covers this where the heads of IT in each dept will work with the NCSC to deploy this security baseline, whatever it is.
Measure 9: The existing ‘Sensor’ Programme will be expanded to all Government Departments, and an assessment will be conducted by the same date as to the feasibility of expanding Sensor to cover all of Government networks.
This genuinely scares me. When I was doing CCNA Cybersecurity Operations, sensors are defined in 5.2.1.8 as;
IDS and IPS technologies share several characteristics, as shown in the figure. IDS and IPS technologies are both deployed as sensors. An IDS or IPS sensor can be in the form of several different devices:
- A router configured with Cisco IOS IPS software
- A device specifically designed to provide dedicated IDS or IPS services
- A network module installed in an adaptive security appliance (ASA), switch, or router
I have also though seen sensors as honeypots or canary tokens but I really hope it's not the traditional definition I know as a sensor because the thought that in 2020, we have government networks that have no IDS or IPS whatsoever is a scary thought... Does that extend as far as firewalls also?! I can't imagine that's the case but I would consider the deployment of both mandatory in this day and age.
Measure 11: The NCSC will be tasked by Government to issue Recommendations with regard to the use of specific software and hardware on Government IT and telecommunications infrastructure.
100% on board with this! But as I said before, maybe we should have thought about this just a little earlier when it came to telecommunications and this might be a great opportunity to look into FOSS and what it could offer as well as what other vendors have to offer.
Measure 12: Government will continue to ensure that second and third level training in computer science and cyber security is developed and deployed, including by supporting the work of Skillnets Ireland in developing training programmes for all educational levels and supporting SOLAS initiatives for ICT apprenticeship programmes in cyber security.
There's not much more to say here. Integrating cyber across all second level and above education, in as broad a spectrum as possible is a commendable initiative! I just wish we had more in the way of detail.
Measure 13: Science Foundation Ireland (SFI) will promote cyber security as a career option in schools and colleges by means of their Smart Futures Programme.
The fact that we aren't speaks volumes.
Measure 14: Science Foundation Ireland along with DBEI and DCCAE, will explore the feasibility through the SFI Research Centre Programme, the Research Centre Spoke programme or other enterprise partnership programmes to fund a significant initiative in Cyber Security Research.
This shouldn't be to explore the feasibility of a Cyber Security Research Centre. This should just simply be to set up a Cyber Security Research Centre. End of. It shouldn't be a question because we want to promote a cyber as public sector, private sector or academic career path, you can't think about it in terms of maybe. It has to be in terms of doing. A combination of this with Measure 15 and Measure 16 could be beneficial as links between the public and private sectors with academia to design and built the technology and do research into what is needed going forward is an important step.
Measure 17: We will reinforce Ireland’s diplomatic commitment to cyber security, including by stationing cyber attachés in key diplomatic missions and by engaging in sustainable capacity building in third countries.
I genuinely think this is fantastic! Hire people to work in a diplomatic capacity to share out skills with the rest of the world! I would drop my life to work on something like this I believe in it so much. It's the cyber equivalent of Peace Keeping and it's a genuinely commendable initiative. I just hope that we can have enough staff so that we can staff all the posts we will need to in Ireland and working on diplomacy globally.
Measure 18: We will create an interdepartmental group (IDG) on internet governance and international cyber policy to coordinate national positions across Departments.
Can we lead a global Arms Control initiative for cyber like we did for nuclear weapons? There's already the start of a framework for this in Microsoft's Digital Geneva Convention and I will totally go and get a Master of Arts in Nonproliferation and Terrorism Studies! I've kinda already been accepted into the course I want to do;
YES!
— Jeffrey Lewis (@ArmsControlWonk) January 16, 2020
Measure 19: We will deepen our existing engagement in international organisations, including by joining the Cyber Security Centre of Excellence (CCD-COE) in Tallinn, Estonia.
I think Rory says all that's need to be said here and I hope we do get a volunteer corps of some kind, though I do think this is a welcome development and something we should do more of. Working alone on the same issues as everyone else
Joining CCD-COE is a welcome development. Sending one person is hardly that revolutionary. An opportunity for the state to doing something really farsighted and leap ahead by embracing the Estonian Cyber Volunteer concept was missed. https://t.co/KPjp5M9g6h pic.twitter.com/POhWzgGSHn
— Rory Byrne (@roryireland) December 27, 2019
What's Missing?
You could say a lot is missing but really... The only thing missing the human factor. There's ideas and technologies that could be implemented, but to run the JSOC, you need people to sit in chairs and analyse events as they arise and you need them there all of the time. There needs to be a rapid scale up in the numbers of people working at the different bodies across the nation on cyber security and national security issues and the only way you're going to get that is by getting the people to work the problem.
And I'm not alone though, I've used Rory Byrne's thread on twitter already in this but the whole thread is worth the read rather than the select few tweets I have shown but I do want to show some more from him as well as others on more stuff that's missing;
There is no mention of recreating the very successful model of the UK NCSC Cyber Security Information Sharing Partnership (CiSP). So a key way to broaden and engage stakeholders from the wider business, NGO etc community on day to day threat sharing is lost.
— Rory Byrne (@roryireland) December 27, 2019
There is no mention of reconfiguring and enhancing state structures such as the Garda and Defence Forces to be able to increase their large gaps in recruitment, training and retention of staff.
— Rory Byrne (@roryireland) December 27, 2019
Regarding education and building the cyber experts of the future. The strategy is lazy and fails to even bother looking at some of the oustanding initiatives across the water. We are patting ourselves on the back for some pretty mediocre resources compared to UK Cyberfirst etc. pic.twitter.com/dkxJISeQo6
— Rory Byrne (@roryireland) December 27, 2019
Wrapping This Up
What I find really frustrating about this strategy is that it appears that behind the scenes that a lot of work has been done by the right people to identify the problems and lay them out in a coherent fashion including an annex of actions, you could almost say I had a glowing review of most elements with all but a few items, like the Guards contract with Eir, where I was at least constructive in my criticism.
But the wheels come off the strategy bus is when you look at the ambition the plan shows in the annex of actions. Some of them come down to just following the law, basically defeatedly saying that we have to because we don't have a choice. Or that we recognize that X is an issue and this will be solved with public information campaigns or with more third level graduates but does not account for the lag time between those graduates coming online and now and how that gap is to be plugged or the recognition that educating the general public on general cyber security matters is a difficult challenge that even experienced professionals fail at a large majority of the time.
And on the education front, maybe we need to look at what other nations are doing like the Cybersecurity Maturity Model Certification (CMMC) in the US. It's a way in which you can begin the process of building a cyber capability within an organization through bootstrapping and adding capabilities over time and requires formal certification to make sure you meet the requirements of each level of the certification. This kind of approach will gradually raise the bar security across the whole sector of defence contractors over time in the US.
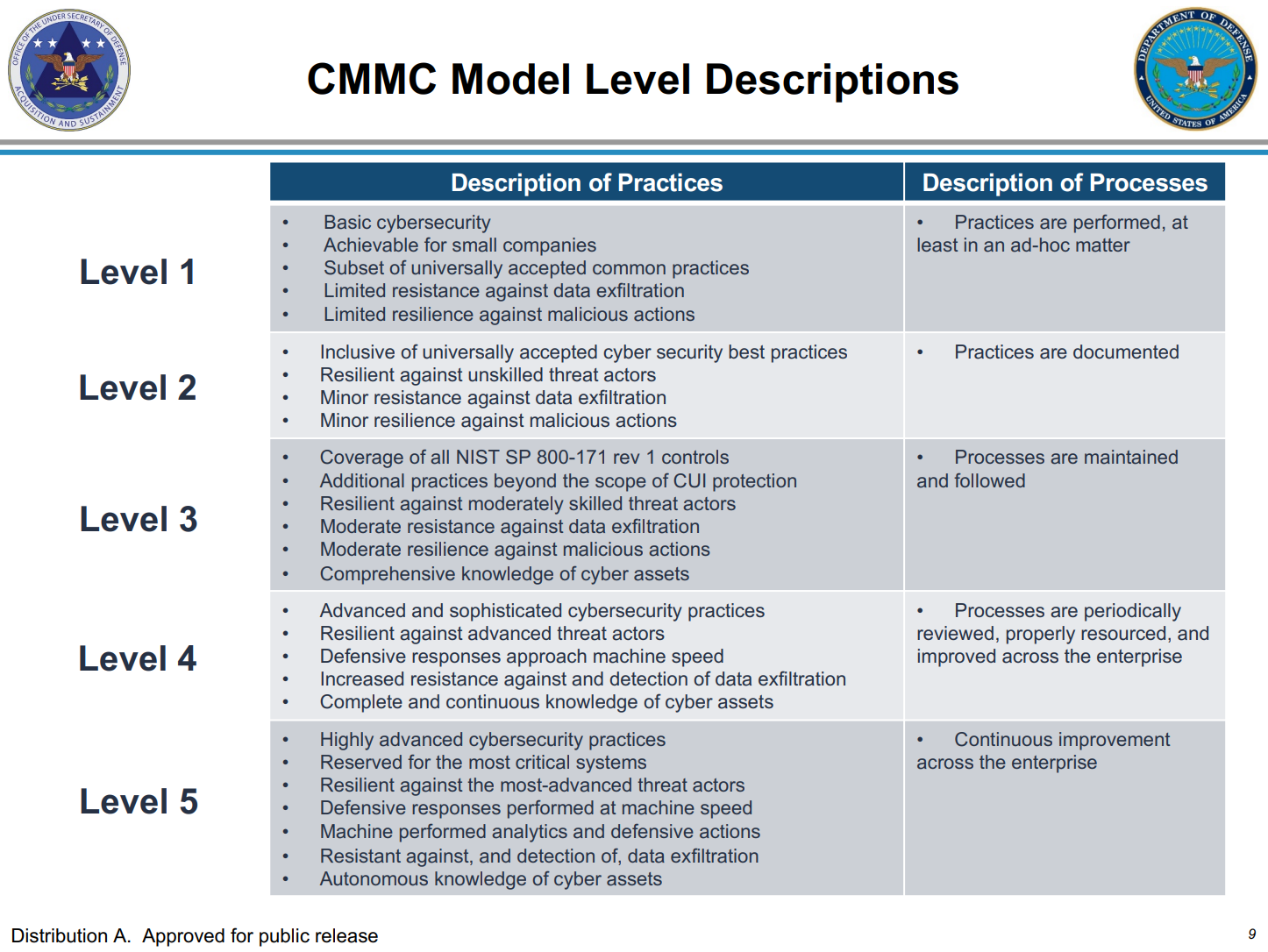
There's no mention of how we could even consider the cost of this or where the money should be raise for it. Or if it's worth using something like the Ireland Strategic Investment Fund to provide funding some of the grand scale, long term projects listed in this. The strategy isn't aware that this might need a strategic funding source that isn't from the daily budgets of the Department of Defence of or the Department of Department of Communications, Climate Action and Environment or the Department of Justice and Equality.
It is a strategy, but it lacks ambition and arguably a grounding in realities of how dynamic information security is and how statically we seem to see the problems at a national level. We realize they are there but we think that they can be solved with little change when historically the implementation of deep and far reaching operational security measures have required organizational sea changes. Or how we plan to integrate cyber into more of what we do since that's what we really need to do, to effectively tackle this issue head on and to be able to think about these issues in the modern, broad sense since it is an issue that effects everyone.
Maybe it's too short term to accomplish wider goals? Maybe I expect too much of what's politically possible in Ireland? Or maybe I see issues like the fact that these missions are spread out across multiple bodies being the issue but the civil service does not? Maybe we should look at utilizing the Department of Defence more fully and make it a full cabinet position again with it's remit being that of National Security and move bodies like the NCSC, NSAC, the Defence Forces and the national security elements of An Garda Síochána all in under one roof? I don't know what all the answers are, but what I do know is that we need to start looking for better answers.
And just to show that I'm not some arsehole on the internet throwing stones at glasses houses, this is an issue I really worry about and I think we are not doing enough on, nor are we really prepared for at a national level and for the betterment of the nation, I will happily give 5 to 10 years and maybe even more, to the NCSC, the NSAC, the Defence Forces, An Garda Síochána, being a CCD-COE representative or working as one of the cyber attachés mentioned in Measure 17, working on these issues in Ireland or with international partners at home or in far flung postings and accept whatever pay cut I have take compared to my fellow graduates when I graduate from college at the end of the current semester because this is the hill I intend to die on.
I have said something to that effect every time I have made this commitment to the above agencies, every time I have met them throughout my time in college and have always been referred to Public Jobs where they never seem to hire anyone. So I will look forward to Slándáil 2020 where I will continue to meet people in these bodies and continue to attempt to join their efforts.